Issues » Server-Side Request Forgery (SSRF) in dotcms/core
| Issue: |
|
|---|---|
| Date: |
|
| Severity: | Medium |
| Requires Admin Access: | Yes |
| Fix Version: | 21.12 |
| Credit: | Vinicius Ribeiro Ferreira da Silva |
| Description: |
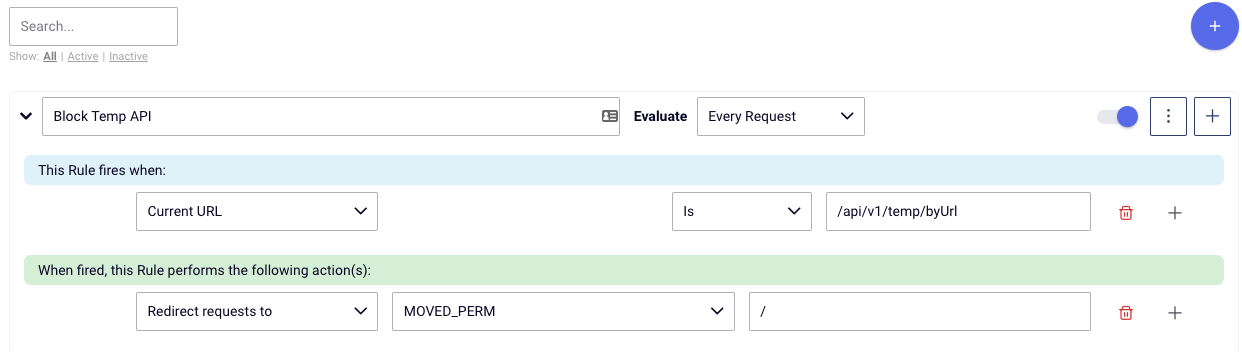
dotCMS TempFileAPI allows a SSRF that can allow to access to internal systems accessible via url
The exploitation can allow access to any web service that can be access via localhost can be target, this include Cloud services like AWS APIs
|
| Mitigation: |
|
| References |
https://huntr.dev/bounties/e903dacf-396c-4c9f-b7b3-3138182a3488/ |